Replace Text in a File Using a Batch Script
Welcome to "Continuous Improvement," the podcast where we explore ways to enhance our productivity, efficiency, and effectiveness. I'm your host, Victor. In today's episode, we'll discuss a clever solution to a common problem. But before we dive in, I want to thank our sponsor, Productivity Pro.
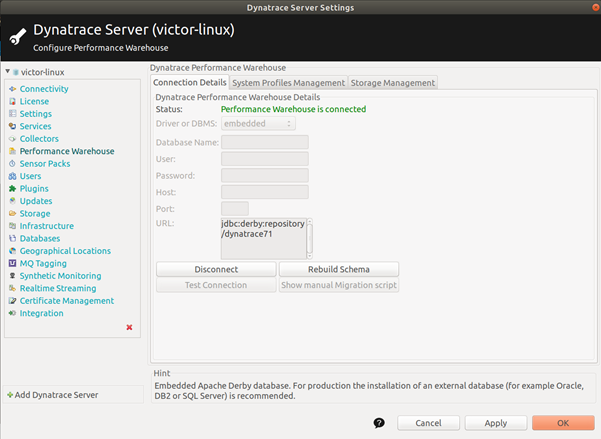
Yesterday, I encountered a situation that many of us can relate to. I was at a client site, working on a Windows server with no internet access. The task at hand was to remove all the id values from YAML files and set them to null. With a large file and no convenient software options, it seemed like a time-consuming task.
But fear not, fellow productivity enthusiasts! I came up with a simple solution that saved me a tremendous amount of time. I wrote a batch script to automate the process. Let me walk you through the steps.
First, in your text editor, create a file called convert.bat. Make sure you have the necessary permissions on your Windows server. Now, let's take a closer look at the script itself.
Inside the convert.bat file, start with the line @echo off. This will suppress the command prompt display, allowing the script to run in the background without cluttering your screen.
Next, we'll use a for loop to read each line of the YAML file. Remember to replace the text temp.yaml with the name of your target input file and result.yaml with the desired output filename.
Within the loop, we check each line for the presence of the id value. If the value is empty, we echo the line without modification. However, if there is an id value present, we check for the phrase " id" using the find command. This ensures that only lines containing id are modified. If the phrase is found, we replace the line with %%a: followed by %%b, effectively setting the id value to null.
Finally, we redirect the output of the script to the desired file using > result.yaml.
And there you have it! By executing this script, you can effortlessly remove id values from YAML files without the need for additional software. It's a simple but effective solution that can save you valuable time and effort.
Remember, continuous improvement is all about finding innovative ways to work smarter, not harder. So next time you encounter a repetitive task, think outside the box and explore scripting or automation options. Who knows, you might just stumble upon a time-saving gem like this batch script.
Well, that wraps up today's episode of "Continuous Improvement." If you found this batch script helpful or have any other tips to share, feel free to reach out to me on social media. Don't forget to tune in next week for another insightful episode.
Until then, stay productive and keep striving for continuous improvement.
Thank you for listening to "Continuous Improvement." This podcast is brought to you by Productivity Pro, your go-to source for all things productivity. Visit our website at productivitypro.com for more resources and tools to supercharge your efficiency. And remember, a little improvement every day goes a long way.
Note: The script mentioned in this episode is for illustration purposes only. Always exercise caution when running scripts on your system and ensure they comply with your organization's policies and security measures.